Explain Different Application of Ip Security
Encryption at the application or the transport layers of the Open Systems Interconnection OSI model can securely transmit data without using IPsec. Secure Socket Layer SSL provides security to the data that is transferred between web browser and server.
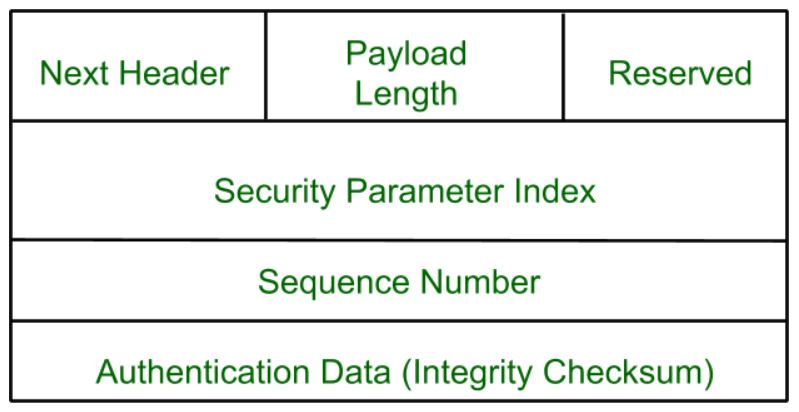
Ipsec Architecture Geeksforgeeks
The term spoofing might have a comic implication in some contexts but its no joke when it comes to information security.
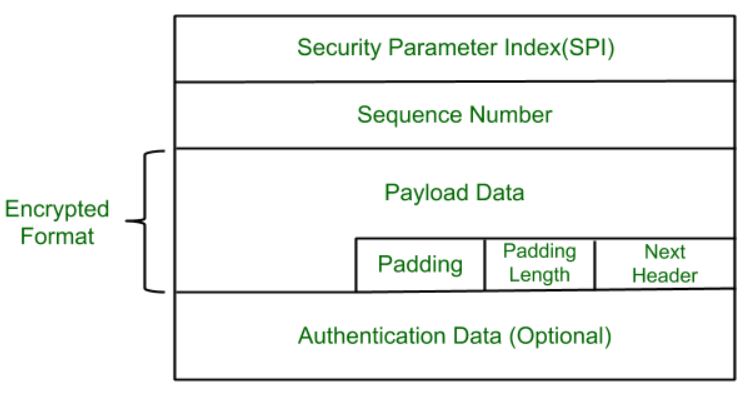
. A collection of frames or pictures are arranged in such a way that it makes the fast movement of pictures. Network layer security controls have been used frequently for securing communications particularly over shared networks such as the Internet because they. These security standards might be applied to the network the operating system application software even programs written by the person who administers your system.
Generally there are several different types of encryption software available that have made the encryption job very easy. Five being the lens size multiplied by zoom gives you maximum mm size of 60 mm. In transport mode the outer header determines the IPsec policy that protects the inner IP packet.
It is a concise version of. With the development and popularization of Internet application technology network security needs. This blog was written by a third party author.
This model acts as a communication protocol for computer networks and connects hosts on the Internet. Last Updated. At the application layer Hypertext.
TCIP applications operate at the application or process layer of the TCPIP hierarchy as discussed in the preceding sectionsTCPIP protocol splits an application. SSL encrypts the link between a web. Secure remote access over the Internet.
It is also one of the applications of digital image processing. Security is a main issue in computing because different kinds of attacks are increasing daily. VoIP network faces a lot of vulnerabilities are subjected to different attacks such as Denial of Service that can be related to one of the following three categories.
Applications of IP Security Secure branch office connectivity over the Internet. The modes differ in policy application when the inner packet is an IP packet as follows. This layer is the abstraction layer which handles the sharing protocols over the computer network with OSI and TCPIP model.
Network Security Network Layer. The TCPIP model is a part of the Internet Protocol Suite. A dynamic packet filter is a firewall facility that can monitor the state of active connections and use this information to determine which network packet s to allow.
Developers can also code applications to reduce. Different types of application security features include authentication authorization encryption logging and application security testing. There is a growing need to protect private information.
In fact this is a subject matter of a whole separate. The Internet was not created with security in mind. Communications can be altered examined and exploited.
Application layer is the last and 7th layer of the OSI model. Here is a list of highly advanced encryption types to know. To secure applications and networks across the OSI stack Imperva provides multi-layered protection to make sure websites and applications are available easily accessible and.
Application security best practices as well as guidance from network security limit access to applications and data to only those who need it. Establishing extranet and intranet connectivity with. The reason here is two fold.
So in our PTZ-LX-700L12X you can multiply 51260. Answer 1 of 3. Finding the right network security tools to secure your sensitive data can be a significant challenge for any organization.
In this case this camera has a.
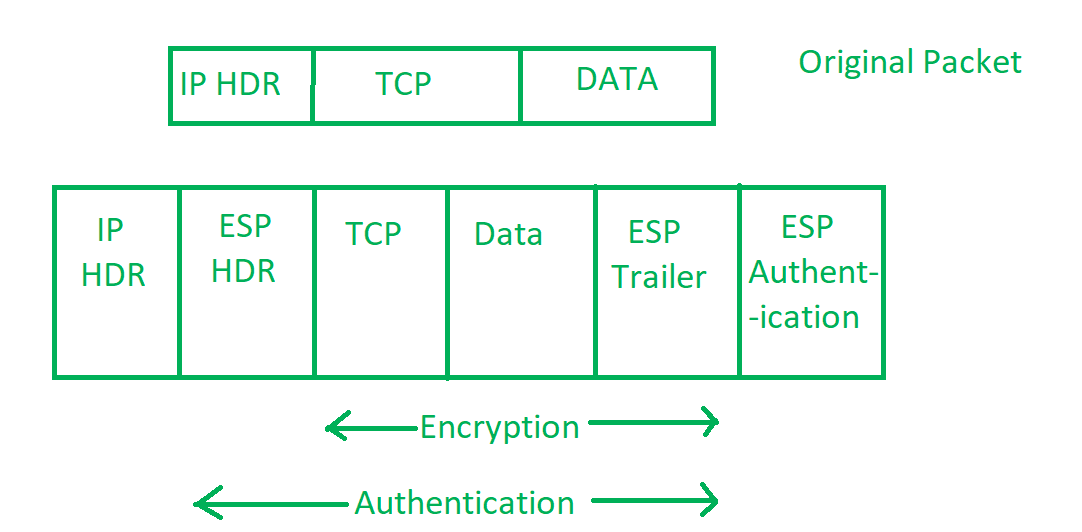
Ip Security Ipsec Geeksforgeeks

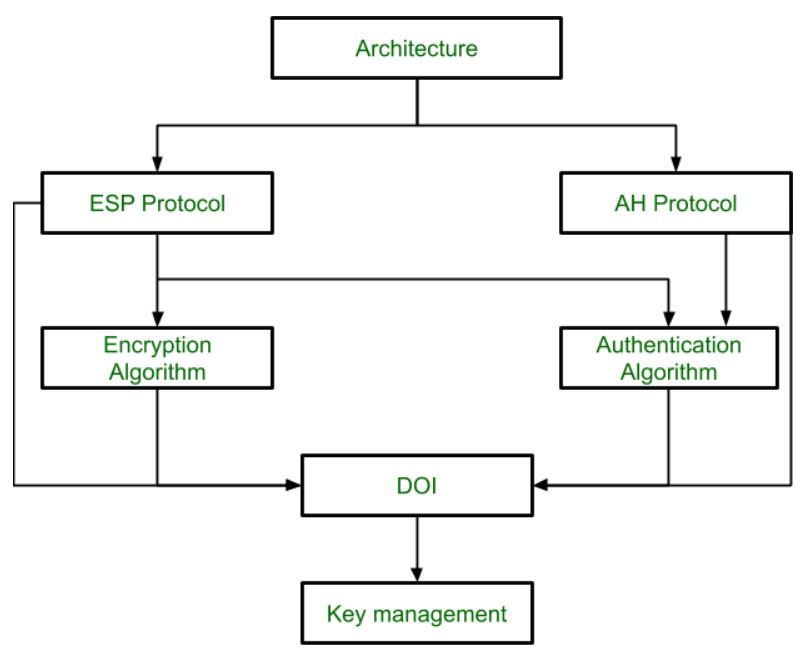
Ipsec Architecture Geeksforgeeks

0 Response to "Explain Different Application of Ip Security"
Post a Comment